Data Security Posture Management Market by End-Use-
· Banking, Financial Services & Insurance (BFSI)
· Healthcare
· Retail & E-Commerce
· IT & ITeS
· Government
· Others
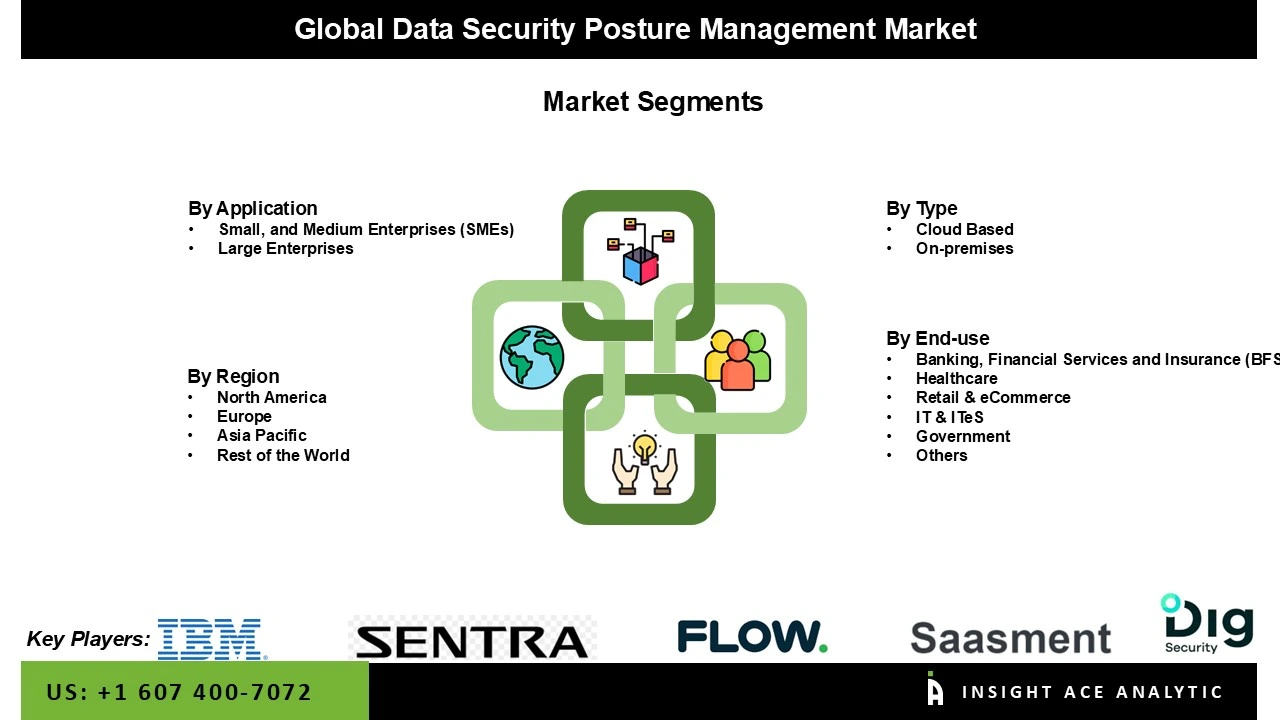
Data Security Posture Management Market by Type-
· On-Premises
· Cloud
Data Security Posture Management Market by Application-
· Small and Medium Enterprises
· Large Enterprises
Data Security Posture Management Market by Region-
North America-
· The US
· Canada
Europe-
· Germany
· The UK
· France
· Italy
· Spain
· Rest of Europe
Asia-Pacific-
· China
· Japan
· India
· South Korea
· Southeast Asia
· Rest of Asia Pacific
Latin America-
· Brazil
· Argentina
· Mexico
· Rest of Latin America
Middle East & Africa-
· GCC Countries
· South Africa
· Rest of the Middle East and Africa
Chapter 1. Methodology and Scope
1.1. Research Methodology
1.2. Research Scope & Assumptions
Chapter 2. Executive Summary
Chapter 3. Global Data Security Posture Management Market Snapshot
Chapter 4. Global Data Security Posture Management Market Variables, Trends & Scope
4.1. Market Segmentation & Scope
4.2. Drivers
4.3. Challenges
4.4. Trends
4.5. Investment and Funding Analysis
4.6. Porter's Five Forces Analysis
4.7. Incremental Opportunity Analysis (US$ MN), 2025-2034
4.8. Global Data Security Posture Management Market Penetration & Growth Prospect Mapping (US$ Mn), 2024-2034
4.9. Competitive Landscape & Market Share Analysis, By Key Player (2024)
4.10. Use/impact of AI on Data Security Posture Management Market Trends
Chapter 5. Data Security Posture Management Market Segmentation 1: By Application, Estimates & Trend Analysis
5.1. Market Share by Application, 2024 & 2034
5.2. Market Size (Value (US$ Mn) & Forecasts and Trend Analyses, 2021 to 2034 for the following Application:
5.2.1. Small, and Medium Enterprises (SMEs)
5.2.2. Large Enterprises
Chapter 6. Data Security Posture Management Market Segmentation 2: By End-Use, Estimates &
Trend Analysis
6.1. Market Share by End-Use, 2024 & 2034
6.2. Market Size (Value (US$ Mn) & Forecasts and Trend Analyses, 2021 to 2034 for the
following End-Use:
6.2.1. Banking, Financial Services and Insurance (BFSI)
6.2.2. Healthcare
6.2.3. Retail & eCommerce
6.2.4. IT & ITeS
6.2.5. Government
6.2.6. Others
Chapter 7. Data Security Posture Management Market Segmentation 3: By Type, Estimates & Trend Analysis
7.1. Market Share by Type, 2024 & 2034
7.2. Market Size (Value (US$ Mn) & Forecasts and Trend Analyses, 2021 to 2034 for the following Type:
7.2.1. Cloud Based
7.2.2. On-premises
Chapter 8. Data Security Posture Management Market Segmentation 4: Regional Estimates & Trend Analysis
8.1. Global Data Security Posture Management Market, Regional Snapshot 2024 & 2034
8.2. North America
8.2.1. North America Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Country, 2021-2034
8.2.1.1. US
8.2.1.2. Canada
8.2.2. North America Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Application, 2021-2034
8.2.3. North America Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by End-Use, 2021-2034
8.2.4. North America Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Type, 2021-2034
8.3. Europe
8.3.1. Europe Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Country, 2021-2034
8.3.1.1. Germany
8.3.1.2. U.K.
8.3.1.3. France
8.3.1.4. Italy
8.3.1.5. Spain
8.3.1.6. Rest of Europe
8.3.2. Europe Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Application, 2021-2034
8.3.3. Europe Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by End-Use, 2021-2034
8.3.4. Europe Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Type, 2021-2034
8.4. Asia Pacific
8.4.1. Asia Pacific Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Country, 2021-2034
8.4.1.1. India
8.4.1.2. China
8.4.1.3. Japan
8.4.1.4. Australia
8.4.1.5. South Korea
8.4.1.6. Hong Kong
8.4.1.7. Southeast Asia
8.4.1.8. Rest of Asia Pacific
8.4.2. Asia Pacific Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Application, 2021-2034
8.4.3. Asia Pacific Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by End-Use, 2021-2034
8.4.4. Asia Pacific Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Type, 2021-2034
8.5. Latin America
8.5.1. Latin America Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Country, 2021-2034
8.5.1.1. Brazil
8.5.1.2. Mexico
8.5.1.3. Rest of Latin America
8.5.2. Latin America Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Application, 2021-2034
8.5.3. Latin America Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by End-Use, 2021-2034
8.5.4. Latin America Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Type, 2021-2034
8.6. Middle East & Africa
8.6.1. Middle East & Africa Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by country, 2021-2034
8.6.1.1. GCC Countries
8.6.1.2. Israel
8.6.1.3. South Africa
8.6.1.4. Rest of Middle East and Africa
8.6.2. Middle East & Africa Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Application, 2021-2034
8.6.3. Middle East & Africa Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by End-Use, 2021-2034
8.6.4. Middle East & Africa Data Security Posture Management Market Revenue (US$ Mn) Estimates and Forecasts by Type, 2021-2034
Chapter 9. Competitive Landscape
9.1. Major Mergers and Acquisitions/Strategic Alliances
9.2. Company Profiles
9.2.1. Wiz, Inc.
9.2.1.1. Business Overview
9.2.1.2. Key Product/Service
9.2.1.3. Financial Performance
9.2.1.4. Geographical Presence
9.2.1.5. Recent Developments with Business Strategy
9.2.2. Palo Alto Networks, Inc.
9.2.3. Microsoft Corporation
9.2.4. Check Point Software Technologies Ltd.
9.2.5. Fortinet, Inc.
9.2.6. CrowdStrike Holdings, Inc.
9.2.7. Cisco Systems, Inc.
9.2.8. Trend Micro Incorporated
9.2.9. Zscaler, Inc.
9.2.10. Tenable Holdings, Inc.
9.2.11. Qualys, Inc.
9.2.12. IBM Corporation
9.2.13. Varonis Systems, Inc.
9.2.14. McAfee, LLC
9.2.15. Digital Guardian, Inc.
9.2.16. Symantec / Broadcom Inc.
9.2.17. Trellix (FireEye/McAfee Enterprise)
9.2.18. Sumo Logic, Inc.
9.2.19. CloudBolt Software, Inc.
9.2.20. Securiti (Securiti.ai, Inc.)
9.2.21. Other Prominent And Emerging Players
This study employed a multi-step, mixed-method research approach that integrates:
This approach ensures a balanced and validated understanding of both macro- and micro-level market factors influencing the market.
Secondary research for this study involved the collection, review, and analysis of publicly available and paid data sources to build the initial fact base, understand historical market behaviour, identify data gaps, and refine the hypotheses for primary research.
Secondary data for the market study was gathered from multiple credible sources, including:
These sources were used to compile historical data, market volumes/prices, industry trends, technological developments, and competitive insights.
Primary research was conducted to validate secondary data, understand real-time market dynamics, capture price points and adoption trends, and verify the assumptions used in the market modelling.
Primary interviews for this study involved:
Interviews were conducted via:
Primary insights were incorporated into demand modelling, pricing analysis, technology evaluation, and market share estimation.
All collected data were processed and normalized to ensure consistency and comparability across regions and time frames.
The data validation process included:
This ensured that the dataset used for modelling was clean, robust, and reliable.
The bottom-up approach involved aggregating segment-level data, such as:
This method was primarily used when detailed micro-level market data were available.
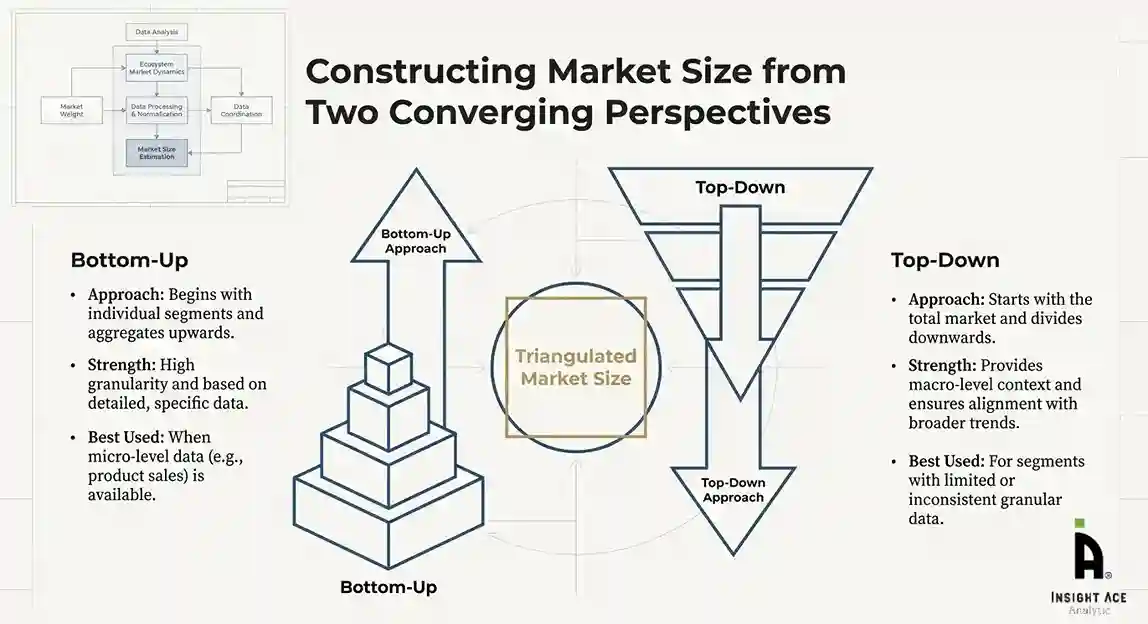
The top-down approach used macro-level indicators:
This approach was used for segments where granular data were limited or inconsistent.
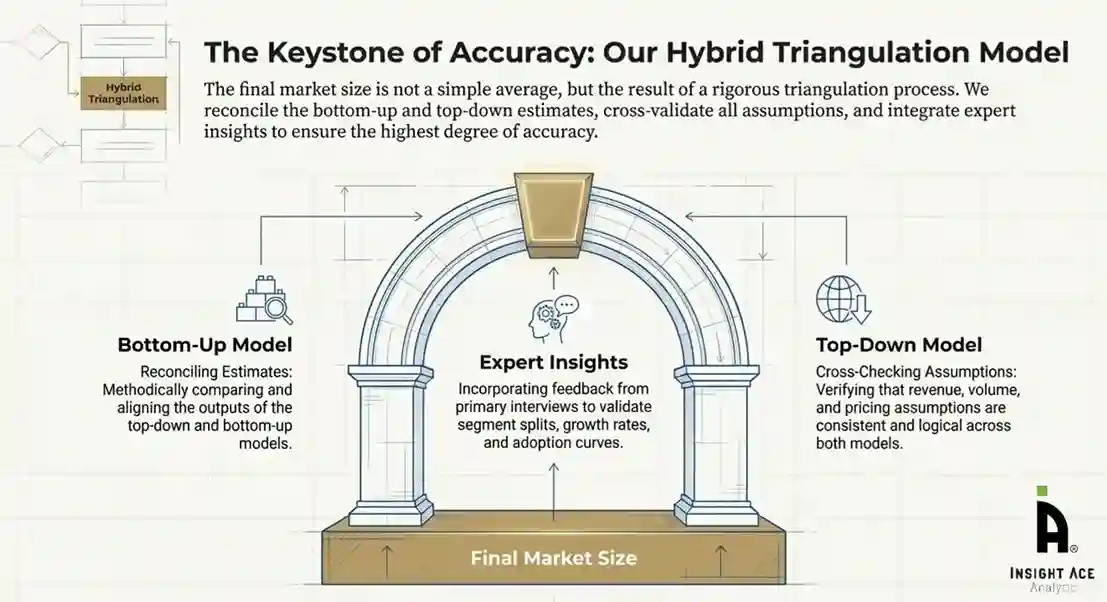
To ensure accuracy, a triangulated hybrid model was used. This included:
This multi-angle validation yielded the final market size.
Market forecasts were developed using a combination of time-series modelling, adoption curve analysis, and driver-based forecasting tools.
Given inherent uncertainties, three scenarios were constructed:
Sensitivity testing was conducted on key variables, including pricing, demand elasticity, and regional adoption.