The Identity Threat Detection and Response (ITDR) Market Size is valued at USD 12.3 Bn in 2023 and is predicted to reach USD 58.0 Bn by the year 2031 at an 21.7% CAGR during the forecast period for 2024-2031.
Identity Threat Detection and Response (ITDR) is a cybersecurity architecture and suite of technologies designed to detect, investigate, and mitigate threats that specifically target identities within an organization's digital environment. It focuses on protecting identity systems, such as privileged access management (PAM), identity and access management (IAM), and authentication services, which control access for users, devices, and applications to sensitive resources. ITDR represents a shift from traditional network perimeter defenses to an identity-centric security approach, which is particularly important as cloud services and remote work have weakened traditional perimeter protections. By monitoring for suspicious activities or anomalies related to user identities, such as unusual login patterns, credential misuse, or unauthorized access, ITDR tools leverage machine learning and behavioral analytics to detect deviations from typical user behavior. This proactive identity-based security framework is essential in safeguarding critical systems from credential-based attacks.
ITDR plays a critical role in helping organizations comply with key data protection regulations such as the EU's General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). GDPR imposes stringent requirements for safeguarding personal data, mandating that organizations implement appropriate technical and organizational measures, and ITDR helps ensure compliance by protecting identity systems. Similarly, HIPAA sets standards for the privacy and security of protected health information (PHI), making ITDR essential for healthcare organizations to prevent unauthorized access, use, or disclosure of PHI. A notable example of ITDR in action is the launch of Semperis' Lightning Identity Runtime Protection in May 2024. This advanced service, based on machine learning, is designed to counter identity attacks such as password spraying and credential stuffing, showcasing how ITDR technology is evolving to address modern cyber threats.
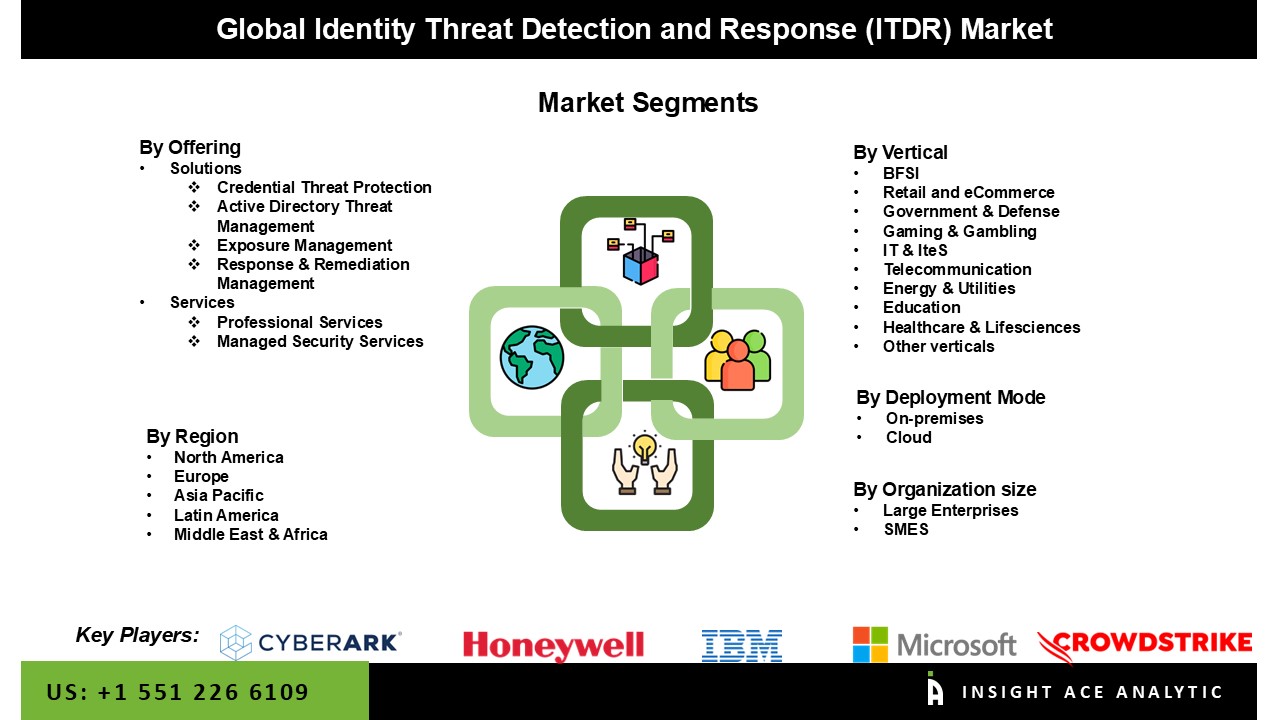
The Identity Threat Detection and Response (ITDR) Market is segmented based on the offering, deployment mode, organization size, vertical. Based on the offering, the market is divided into solutions and services. Based on the deployment mode, the market is divided cloud and on-premises. Based on the vertical, the market is divided into BFSI, retail and ecommerce, government & defense, gaming & gambling, it & ites, telecommunication, energy & utilities, education, healthcare &, lifesciences, other verticals. Based on organization size, the market is divided into large enterprises, SMES.
Based on the offering, the market is divided into solutions and services. Among these, the solution segment is expected to have the highest growth rate during the forecast period. The market is dominated by the solutions category because of its capacity to provide countermeasures against identity-based threats, such as password leaks and hacked user accounts. This is accomplished by quickly detecting any suspicious behavior through ongoing monitoring of user activity and access management logs. To improve the efficacy of the solution, additional data is collected from many identities and access management (IAM) sources. This includes gathering system logs and network traffic data to monitor and analyze it on endpoint devices such as workstations and laptops.
Based on the deployment mode, the market is divided cloud and on-premises. the cloud segment dominates the market. Cloud-based ITDR solutions often have lower upfront costs and reduced maintenance needs since they do not require extensive on-premises infrastructure. Many organizations prefer cloud-based models because they offer a subscription-based pricing structure, which lowers capital expenditure and shifts to an operational expenditure model. In contrast, on-premises solutions typically involve higher costs for hardware, software, and ongoing management. Cloud ITDR solutions often integrate more easily with existing cloud-based tools such as cloud identity and access management (IAM) platforms, security information and event management (SIEM) systems, and other security services. This ease of integration makes cloud-based ITDR solutions a more efficient choice for organizations already operating in the cloud.
North America, particularly the United States, faces a high volume of cyberattacks, including identity-based attacks such as credential theft, phishing, and privilege escalation. With cyber threats becoming increasingly sophisticated, organizations in North America are highly motivated to invest in robust ITDR solutions to protect identities and mitigate risks. North America is often at the forefront of adopting advanced technologies like cloud computing, artificial intelligence (AI), and machine learning (ML). ITDR solutions, which leverage AI and ML for identity-based threat detection, align well with the technological landscape in the region. The adoption of cloud-based solutions in North America is particularly high, which drives demand for ITDR systems that protect cloud environments.
|
Report Attribute |
Specifications |
|
Market Size Value In 2023 |
USD 12.3 Bn |
|
Revenue Forecast In 2031 |
USD 58.0 Bn |
|
Growth Rate CAGR |
CAGR of 21.7% from 2024 to 2031 |
|
Quantitative Units |
Representation of revenue in US$ Bn and CAGR from 2024 to 2031 |
|
Historic Year |
2019 to 2023 |
|
Forecast Year |
2024-2031 |
|
Report Coverage |
The forecast of revenue, the position of the company, the competitive market structure, growth prospects, and trends |
|
Segments Covered |
By Offering, By Deployment Mode, By Organization Size, By Vertical |
|
Regional Scope |
North America; Europe; Asia Pacific; Latin America; Middle East & Africa |
|
Country Scope |
U.S.; Canada; U.K.; Germany; China; India; Japan; Brazil; Mexico; France; Italy; Spain; South Korea; South East Asia |
|
Competitive Landscape |
Microsoft, Ibm, Crowdstrike, Zscaler, Tenable, Varonis, Beyondtrust, Cyberark, Proofpoint, Quest, Oort (Cisco), Sentinelone, Vectra, Proficio, Qomplx, Adaptive Shield, Acalvio, Authomize, Illusive, Mindfire, Rezonate, Semperis, Silverfort, Stealthbits, Vericlouds, Microminder, Quorum Cyber, Mixmode, ZeroFox, Honeywell, Zimperium, Okta AI, Cisco, One Identity |
|
Customization Scope |
Free customization report with the procurement of the report and modifications to the regional and segment scope. Particular Geographic competitive landscape. |
|
Pricing and Available Payment Methods |
Explore pricing alternatives that are customized to your particular study requirements. |
Chapter 1. Methodology and Scope
1.1. Research Methodology
1.2. Research Scope & Assumptions
Chapter 2. Executive Summary
Chapter 3. Global Identity Threat Detection and Response (ITDR) Market Snapshot
Chapter 4. Global Identity Threat Detection and Response (ITDR) Market Variables, Trends & Scope
4.1. Market Segmentation & Scope
4.2. Drivers
4.3. Challenges
4.4. Trends
4.5. Investment and Funding Analysis
4.6. Porter's Five Forces Analysis
4.7. Incremental Opportunity Analysis (US$ MN), 2024-2031
4.8. Global Identity Threat Detection and Response (ITDR) Market Penetration & Growth Prospect Mapping (US$ Mn), 2023-2031
4.9. Competitive Landscape & Market Share Analysis, By Key Player (2023)
4.10. Use/impact of AI on Identity Threat Detection and Response (ITDR) Industry Trends
Chapter 5. Identity Threat Detection and Response (ITDR) Market Segmentation 1: By Offering, Estimates & Trend Analysis
5.1. Market Share by Offering, 2023 & 2031
5.2. Market Size (Value US$ Mn) & Forecasts and Trend Analyses, 2019 to 2031 for the following Offering:
5.2.1. Solutions
5.2.1.1. Credential Threat Protection
5.2.1.2. Active Directory Threat Management
5.2.1.3. Exposure Management
5.2.1.4. Response & Remediation Management
5.2.2. Services
5.2.2.1. Professional Services
5.2.2.2. Managed Security Services
Chapter 6. Identity Threat Detection and Response (ITDR) Market Segmentation 2: By Deployment Mode, Estimates & Trend Analysis
6.1. Market Share by Deployment Mode, 2023 & 2031
6.2. Market Size (Value US$ Mn) & Forecasts and Trend Analyses, 2019 to 2031 for the following Deployment Modes:
6.2.1. On-premises
6.2.2. Cloud
Chapter 7. Identity Threat Detection and Response (ITDR) Market Segmentation 3: By Organization Size, Estimates & Trend Analysis
7.1. Market Share by Organization Size, 2023 & 2031
7.2. Market Size (Value US$ Mn) & Forecasts and Trend Analyses, 2019 to 2031 for the following Organization Sizes:
7.2.1. Large Enterprises
7.2.2. SMES
Chapter 8. Identity Threat Detection and Response (ITDR) Market Segmentation 4: By Vertical, Estimates & Trend Analysis
8.1. Market Share by Vertical, 2023 & 2031
8.2. Market Size (Value US$ Mn) & Forecasts and Trend Analyses, 2019 to 2031 for the following Verticals:
8.2.1. BFSI
8.2.2. Retail and eCommerce
8.2.3. Government & Defense
8.2.4. Gaming & Gambling
8.2.5. IT & IteS
8.2.6. Telecommunication
8.2.7. Energy & Utilities
8.2.8. Education
8.2.9. Healthcare & Lifesciences
8.2.10. Other verticals
Chapter 9. Identity Threat Detection and Response (ITDR) Market Segmentation 5: Regional Estimates & Trend Analysis
9.1. Global Identity Threat Detection and Response (ITDR) Market, Regional Snapshot 2023 & 2031
9.2. North America
9.2.1. North America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Country, 2024-2031
9.2.1.1. US
9.2.1.2. Canada
9.2.2. North America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Offering, 2024-2031
9.2.3. North America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Deployment Mode, 2024-2031
9.2.4. North America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Organization Size, 2024-2031
9.2.5. North America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Vertical, 2024-2031
9.3. Europe
9.3.1. Europe Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Country, 2024-2031
9.3.1.1. Germany
9.3.1.2. U.K.
9.3.1.3. France
9.3.1.4. Italy
9.3.1.5. Spain
9.3.1.6. Rest of Europe
9.3.2. Europe Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Offering, 2024-2031
9.3.3. Europe Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Deployment Mode, 2024-2031
9.3.4. Europe Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Organization Size, 2024-2031
9.3.5. Europe Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Vertical, 2024-2031
9.4. Asia Pacific
9.4.1. Asia Pacific Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Country, 2024-2031
9.4.1.1. India
9.4.1.2. China
9.4.1.3. Japan
9.4.1.4. Australia
9.4.1.5. South Korea
9.4.1.6. Hong Kong
9.4.1.7. Southeast Asia
9.4.1.8. Rest of Asia Pacific
9.4.2. Asia Pacific Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Offering, 2024-2031
9.4.3. Asia Pacific Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Deployment Mode, 2024-2031
9.4.4. Asia Pacific Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts By Organization Size, 2024-2031
9.4.5. Asia Pacific Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Vertical, 2024-2031
9.5. Latin America
9.5.1. Latin America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Country, 2024-2031
9.5.1.1. Brazil
9.5.1.2. Mexico
9.5.1.3. Rest of Latin America
9.5.2. Latin America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Offering, 2024-2031
9.5.3. Latin America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Deployment Mode, 2024-2031
9.5.4. Latin America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Organization Size, 2024-2031
9.5.5. Latin America Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Vertical, 2024-2031
9.6. Middle East & Africa
9.6.1. Middle East & Africa Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by country, 2024-2031
9.6.1.1. GCC Countries
9.6.1.2. Israel
9.6.1.3. South Africa
9.6.1.4. Rest of Middle East and Africa
9.6.2. Middle East & Africa Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Offering, 2024-2031
9.6.3. Middle East & Africa Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Deployment Mode, 2024-2031
9.6.4. Middle East & Africa Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Organization Size, 2024-2031
9.6.5. Middle East & Africa Identity Threat Detection and Response (ITDR) Market Revenue (US$ Million) Estimates and Forecasts by Vertical, 2024-2031
Chapter 10. Competitive Landscape
10.1. Major Mergers and Acquisitions/Strategic Alliances
10.2. Company Profiles
10.2.1. . Microsoft
10.2.1.1. Business Overview
10.2.1.2. Key Product/Service Offerings
10.2.1.3. Financial Perofferingance
10.2.1.4. Geographical Presence
10.2.1.5. Recent Developments with Business Strategy
10.2.2. IBM
10.2.3. Crowdstrike
10.2.4. Zscaler
10.2.5. Tenable
10.2.6. Varonis
10.2.7. Beyondtrust
10.2.8. Cyberark
10.2.9. Proofpoint
10.2.10. Quest
10.2.11. Oort (Cisco)
10.2.12. Sentinelone
10.2.13. Vectra
10.2.14. Proficio
10.2.15. Qomplx
10.2.16. Adaptive Shield
10.2.17. Acalvio
10.2.18. Authomize
10.2.19. Illusive
10.2.20. Mindfire
10.2.21. Rezonate
10.2.22. Semperis
10.2.23. Silverfort
10.2.24. Stealthbits
10.2.25. Vericlouds
10.2.26. Microminder
10.2.27. Quorum Cyber
10.2.28. Mixmode
10.2.29. ZeroFox
10.2.30. Honeywell
10.2.31. Zimperium
10.2.32. Okta AI
10.2.33. Cisco
10.2.34. One Identity
10.2.35. Other Market Players
Global Identity Threat Detection and Response (ITDR) Market- By Offering
Global Identity Threat Detection and Response (ITDR) Market – By Deployment mode
Global Identity Threat Detection and Response (ITDR) Market – By Organization size
Global Identity Threat Detection and Response (ITDR) Market – By Vertical
Global Identity Threat Detection and Response (ITDR) Market – By Region
North America-
Europe-
Asia-Pacific-
Latin America-
Middle East & Africa-
InsightAce Analytic follows a standard and comprehensive market research methodology focused on offering the most accurate and precise market insights. The methods followed for all our market research studies include three significant steps – primary research, secondary research, and data modeling and analysis - to derive the current market size and forecast it over the forecast period. In this study, these three steps were used iteratively to generate valid data points (minimum deviation), which were cross-validated through multiple approaches mentioned below in the data modeling section.
Through secondary research methods, information on the market under study, its peer, and the parent market was collected. This information was then entered into data models. The resulted data points and insights were then validated by primary participants.
Based on additional insights from these primary participants, more directional efforts were put into doing secondary research and optimize data models. This process was repeated till all data models used in the study produced similar results (with minimum deviation). This way, this iterative process was able to generate the most accurate market numbers and qualitative insights.
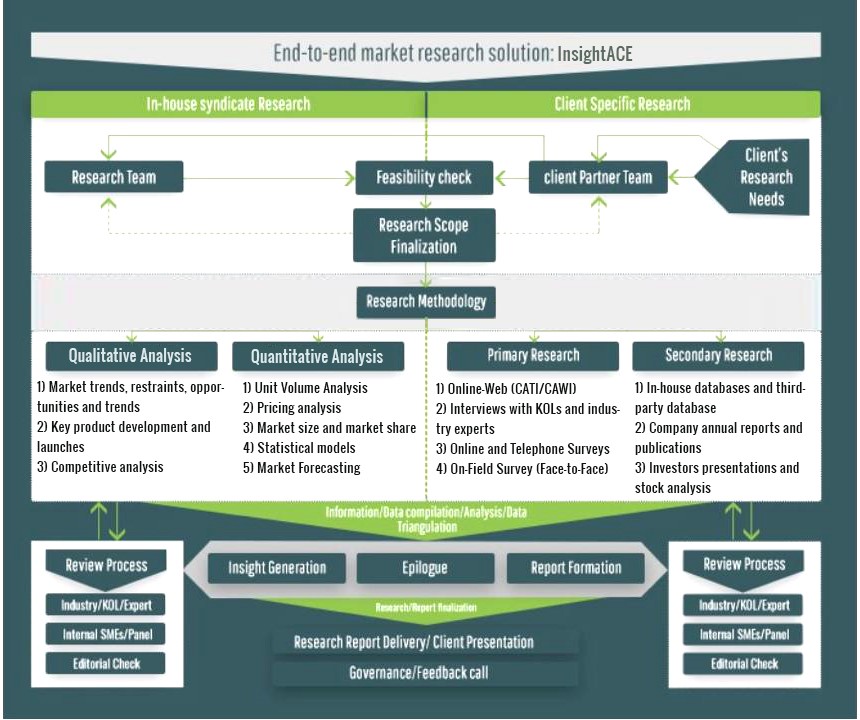
Secondary research
The secondary research sources that are typically mentioned to include, but are not limited to:
The paid sources for secondary research like Factiva, OneSource, Hoovers, and Statista
Primary Research:
Primary research involves telephonic interviews, e-mail interactions, as well as face-to-face interviews for each market, category, segment, and subsegment across geographies
The contributors who typically take part in such a course include, but are not limited to:
Data Modeling and Analysis:
In the iterative process (mentioned above), data models received inputs from primary as well as secondary sources. But analysts working on these models were the key. They used their extensive knowledge and experience about industry and topic to make changes and fine-tuning these models as per the product/service under study.
The standard data models used while studying this market were the top-down and bottom-up approaches and the company shares analysis model. However, other methods were also used along with these – which were specific to the industry and product/service under study.