The Zero Trust Network Access Market Size is predicted to expand at an 14.88% CAGR during the forecast period for 2024-2031.
Zero Trust Network Access (ZTNA) is a modern cybersecurity framework designed to enhance security in increasingly complex IT environments. Unlike traditional security models that rely on a secure perimeter, ZTNA operates on the principle that no user or device should be trusted by default, regardless of their location. This approach ensures that access to applications and data is granted based on strict identity verification and contextual factors, significantly reducing the risk of unauthorized access and data breaches. ZTNA is primarily utilized to secure remote access to applications, especially as organizations increasingly adopt cloud services and support remote workforces. Its applications include enabling employees to access corporate applications and data securely from any location, thus supporting remote work and collaboration without compromising security.
One of the primary driving factors behind the growth of the ZTNA market is the increasing adoption of cloud computing. As organizations migrate to cloud environments, the need for robust security measures that can protect sensitive data and applications from potential threats becomes paramount. ZTNA provides a framework that aligns with cloud architectures, allowing businesses to implement security controls that are both flexible and scalable. This facilitates a secure transition to cloud-based operations, ensuring that businesses can protect their assets while leveraging the benefits of the cloud.
The Zero Trust Network Access market is type of product, type of drug discovery steps, type of therapeutic area, and company size. By type of product the market is segmented into synthetic peptides, biological and recombinant peptides, and macrocycles. By drug discovery steps market is categorized into target identification and validation, hit identification, lead generation, and lead optimization. By therapeutic area market is categorized into oncological disorders, metabolic disorders, cardiovascular disorders, infectious disorders, urological disorders, endocrine disorders, CNS disorders, and other diseases. By company size the market is categorized into small, mid-sized and large and very large companies.
The ZTNA-As-A-Service segment is significantly driving the Zero Trust Network Access (ZTNA) market due to its alignment with contemporary security needs and technological advancements. Key drivers include the increasing adoption of cloud computing, which necessitates flexible and scalable security solutions, and the rise of remote work, which demands secure and adaptable access controls. ZTNA-As-A-Service allows organizations to secure remote access to cloud-hosted applications without the complexities of traditional on-premises solutions, reducing risks associated with remote connections. Additionally, its cost-effectiveness eliminates the need for significant upfront investments in hardware and infrastructure, appealing particularly to small and medium-sized enterprises that benefit from scalable and quickly deployable solutions.
The Zero Trust Network Access (ZTNA) market is experiencing significant growth, particularly driven by the Cloud deployment segment due to its flexibility, scalability, cost efficiency, and rapid deployment capabilities. Cloud deployment allows organizations to scale network resources easily, adapt to changing operational requirements without the constraints of physical hardware, and adopt a pay-as-you-go model, making it financially attractive, especially for small and medium enterprises. The rise of remote work necessitates secure access solutions for a distributed workforce, and cloud-based ZTNA solutions provide secure, seamless access from anywhere, integrating well with existing IT environments without requiring extensive infrastructure overhauls.
North America leads the Zero Trust Network Access (ZTNA) market due to high adoption of advanced technologies, growing cybersecurity concerns, significant investment in cloud infrastructure, and stringent regulatory compliance requirements. The region's strong presence of technology companies and high rate of implementing advanced security solutions, particularly in the United States, drive ZTNA adoption. Rising incidents of data breaches and cyberattacks prompt businesses to prioritize the zero trust model for effective risk mitigation. Additionally, the shift towards cloud computing and the need for scalable, flexible security solutions fuel demand for cloud-based ZTNA. Regulatory requirements for data protection and privacy further compel organizations to adopt robust security measures, including ZTNA.
| Report Attribute | Specifications |
| Growth Rate CAGR | CAGR of 14.88 % from 2024 to 2031 |
| Quantitative Units | Representation of revenue in US$ Bn and CAGR from 2024 to 2031 |
| Historic Year | 2019 to 2023 |
| Forecast Year | 2024-2031 |
| Report Coverage | The forecast of revenue, the position of the company, the competitive market structure, growth prospects, and trends |
| Segments Covered | By Model, Deployment, Approach, Enterprise Size |
| Regional Scope | North America; Europe; Asia Pacific; Latin America; Middle East & Africa |
| Country Scope | U.S.; Canada; U.K.; Germany; China; India; Japan; Brazil; Mexico; The UK; France; Italy; Spain; China; Japan; India; South Korea; Southeast Asia; South Korea; Southeast Asia |
| Competitive Landscape | Banyan Security, BlackRidge Technology, Certes Networks, Check Point Software Technologies Ltd., Citrix Systems, Cloudflare Inc., Cyxtera Technologies, Forcepoint (Fransisco Partners), Fortinet Inc., Google, Hewlett Packard Enterprise, Ivanti, Palo Alto Networks, Pulse Secure, Safe-T Data, Sopho Limited, Systancia, Unisys Security, Versa Networks Inc., VMWare Inc., Waverley Labs, Zentera Systems, Zscaler Inc |
| Customization Scope | Free customization report with the procurement of the report, Modifications to the regional and segment scope. Geographic competitive landscape. |
| Pricing and Available Payment Methods | Explore pricing alternatives that are customized to your particular study requirements. |
Zero Trust Network Access Market by Model -
Zero Trust Network Access Market by Deployment -
Zero Trust Network Access Market by Approach-
Zero Trust Network Access Market by Enterprise Size -
Zero Trust Network Access Market by Region-
North America-
Europe-
Asia-Pacific-
Latin America-
Middle East & Africa-
This study employed a multi-step, mixed-method research approach that integrates:
This approach ensures a balanced and validated understanding of both macro- and micro-level market factors influencing the market.
Secondary research for this study involved the collection, review, and analysis of publicly available and paid data sources to build the initial fact base, understand historical market behaviour, identify data gaps, and refine the hypotheses for primary research.
Secondary data for the market study was gathered from multiple credible sources, including:
These sources were used to compile historical data, market volumes/prices, industry trends, technological developments, and competitive insights.
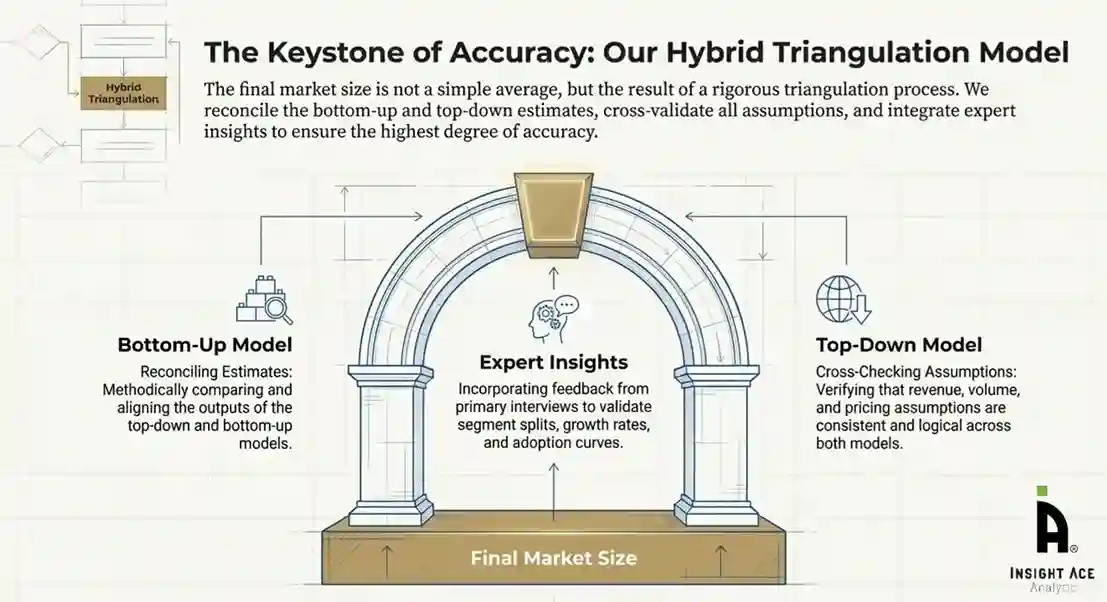
Primary research was conducted to validate secondary data, understand real-time market dynamics, capture price points and adoption trends, and verify the assumptions used in the market modelling.
Primary interviews for this study involved:
Interviews were conducted via:
Primary insights were incorporated into demand modelling, pricing analysis, technology evaluation, and market share estimation.
All collected data were processed and normalized to ensure consistency and comparability across regions and time frames.
The data validation process included:
This ensured that the dataset used for modelling was clean, robust, and reliable.
The bottom-up approach involved aggregating segment-level data, such as:
This method was primarily used when detailed micro-level market data were available.
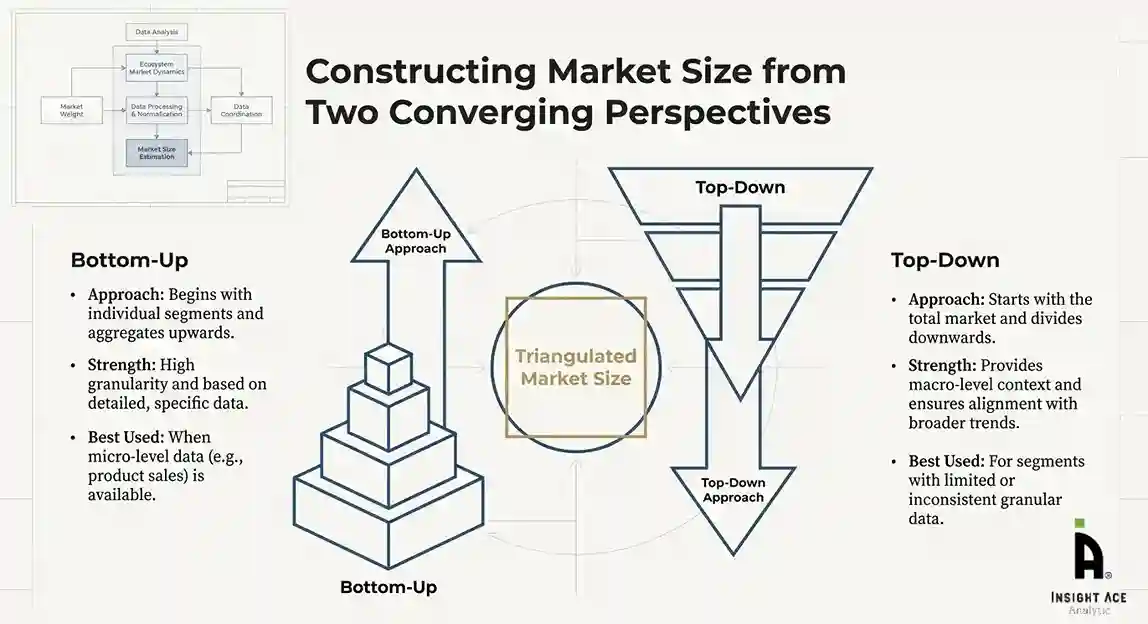
The top-down approach used macro-level indicators:
This approach was used for segments where granular data were limited or inconsistent.
To ensure accuracy, a triangulated hybrid model was used. This included:
This multi-angle validation yielded the final market size.
Market forecasts were developed using a combination of time-series modelling, adoption curve analysis, and driver-based forecasting tools.
Given inherent uncertainties, three scenarios were constructed:
Sensitivity testing was conducted on key variables, including pricing, demand elasticity, and regional adoption.